I posted my password / API key on GitHub
Or GitLab, or any other public source control management platform. Now what?
I stumbled on a website that continuously scans GitHub, GitLab and BitBucket, the 3 most common places to host source code publicly, and shows you committed SSH passwords, API keys for common services, databases and so on.
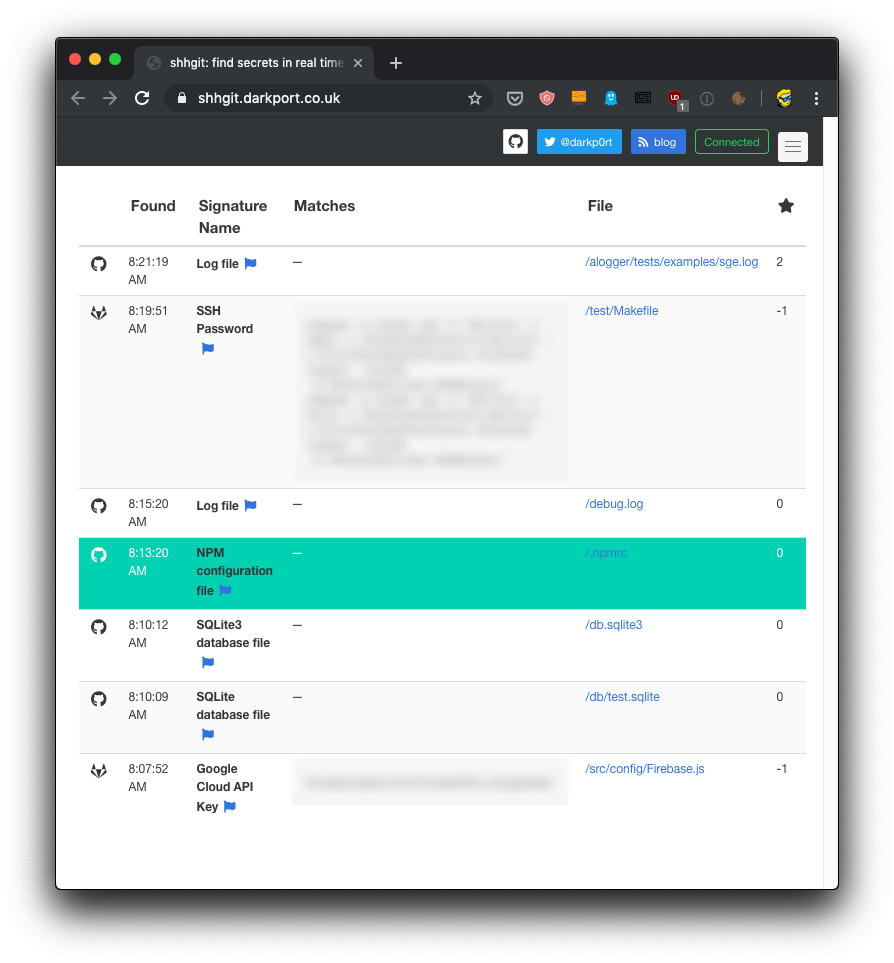
It’s scary, right?
Raise your hand if it never happened to you. We can make mistakes. And when this happens, there’s no other way than quickly invalidating the password or API key that was exposed to the public.
For people new to Git: you can’t just rollback the commit, because it will still be kept in the history of the repository.
Your reputation, the reputation of your project, the security of your users is at stake.
After you fix the emergency, the issue is: how to prevent the problem? What’s the answer? What’s the solution that can help us avoid commit secrets to a publicly available Git repository?
The answer is: workflow and tooling.
First, never add your API keys or passwords inside source code. They can hide in there, quietly. Instead, always add them to a .env file in the project root folder, and add .env to your .gitignore file, so it will never be committed. Use a tool like dotenv to access them.
Use git-secrets, a tool that will help you avoid committing secrets to Git.
In macOS you install it using Homebrew:
brew install git-secretsthen go inside the repository you want to activate it on, and run
git secrets --installto install the Git pre-commit hook. This will ensure the tool runs before Git makes the commit to the repo.
If you use Amazon Web Services (AWS), run this command to add the set of patterns used by that services credentials:
git secrets --register-awsYou can immediately scan for issues using
git secrets --scanIdeally the tool should not print anything. But if you have issues, it will give you plenty of details.
download all my books for free
- javascript handbook
- typescript handbook
- css handbook
- node.js handbook
- astro handbook
- html handbook
- next.js pages router handbook
- alpine.js handbook
- htmx handbook
- react handbook
- sql handbook
- git cheat sheet
- laravel handbook
- express handbook
- swift handbook
- go handbook
- php handbook
- python handbook
- cli handbook
- c handbook
subscribe to my newsletter to get them
Terms: by subscribing to the newsletter you agree the following terms and conditions and privacy policy. The aim of the newsletter is to keep you up to date about new tutorials, new book releases or courses organized by Flavio. If you wish to unsubscribe from the newsletter, you can click the unsubscribe link that's present at the bottom of each email, anytime. I will not communicate/spread/publish or otherwise give away your address. Your email address is the only personal information collected, and it's only collected for the primary purpose of keeping you informed through the newsletter. It's stored in a secure server based in the EU. You can contact Flavio by emailing flavio@flaviocopes.com. These terms and conditions are governed by the laws in force in Italy and you unconditionally submit to the jurisdiction of the courts of Italy.